The cybersecurity landscape is massively expanding while attack strategies keep evolving, fueling the cybercrime epidemic. Cyber threats evolved from targeting and harming computers, networks, and smartphones — to humans, cars, railways, planes, power grids and anything with an electronic pulse. Expectations are that cybercrime damages cost the world 10.5 trillion US dollars by 2025. And in general, the belief is that cybercrime costs will grow 15% per year over the next five years.
This growth is powered by the Internet of Things. Forbes expects there to be 75 billion smart devices in the world by 2025. Unfortunately, securing devices and objects such as cars, medical instruments, sensors, manufacturing machines, home appliances and phones that could be ‘talking’ to each other, is a major challenge for the years to come.
The largest impact on cyberspace in 2022 has been the war between Russia and Ukraine. And this will most likely continue in 2023. According to Forbes, immediately after the conflict broke out, suspected Russian-sourced cyberattacks were observed over a 48-hour period with an increase of 800%. Also in the upcoming year, we need to keep our eyes open for international attacks such as ATPs, malware, ransomware, DDoS and network attacks.
Next to this, cybercriminals continue to leverage the impact of the COVID-19 pandemic. In the last two years, they adapted their attack strategy to exploit vaccination mandates, elections and the shift to hybrid work. These criminals want to target organisations' supply chains and networks for them to achieve maximum disruption, also for the coming year. Cybercriminals will also find new opportunities for attack with deepfakes, cryptocurrency, mobile wallets and more.
Cybersecurity companies provide solutions and services that are increasingly committed to preventing just that. With that in mind, we’ve listed the top cybersecurity companies for you to watch in 2023.
Fortinet
Fortinet is recognised in the Forrester Wave™ of Enterprise Firewalls as a leader in Q4 2022 with their NGFW FortiGuard. Also by Gartner, they were named a Leader for Network Firewalls 12 times. The company has over 615,000 customers around the world and has a broad portfolio covering secure SD-WAN, cloud security, network security, application security, email security, and secure access, all supported with a single pane of glass management across the entire attack surface.
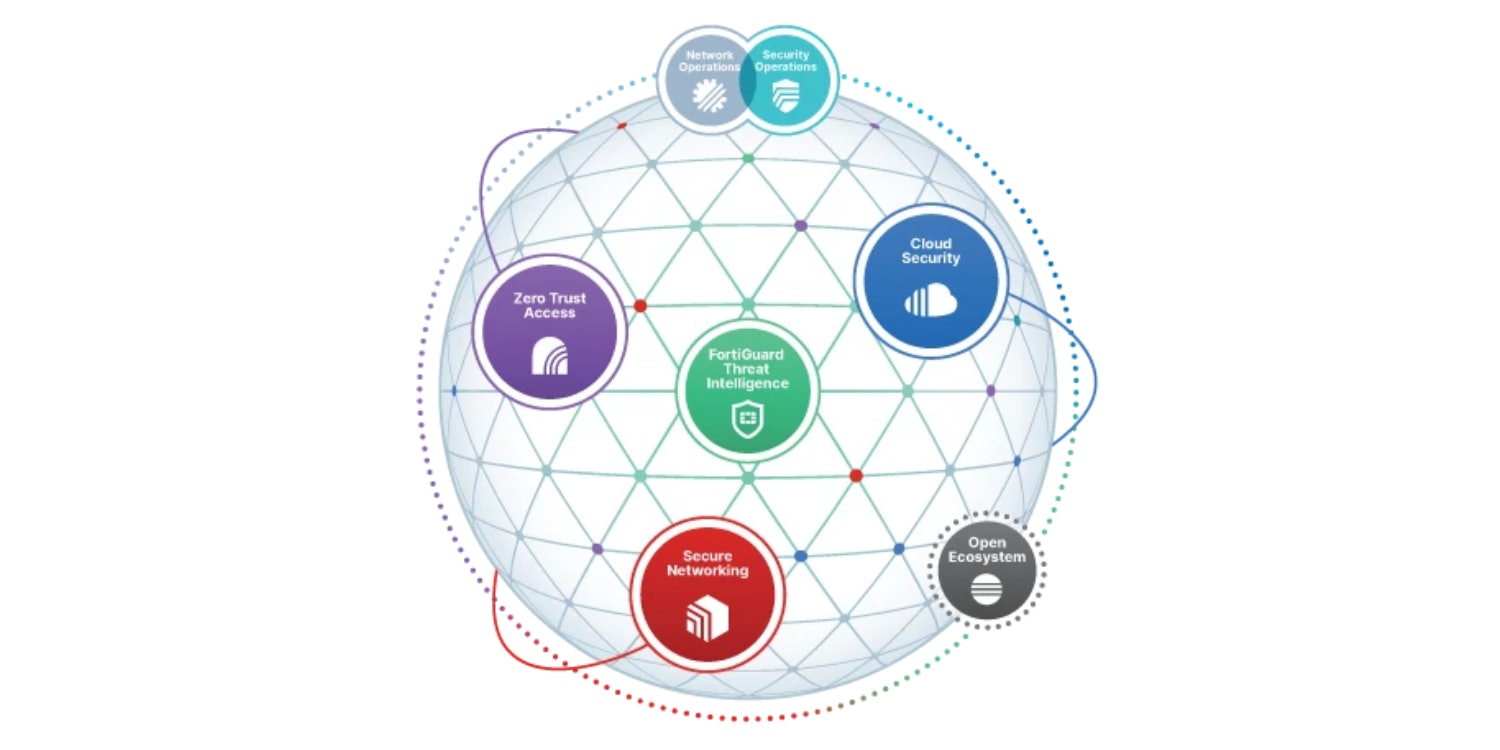
With their Fortinet Security Fabric, they provide a cybersecurity mesh platform powered by FortiOS. The Security Fabric spans the extended digital attack surface and cycle, enabling self-healing security and networking to protect devices, data, and applications. It also brings together the concepts of convergence and consolidation to provide comprehensive real-time cybersecurity protection from users to applications.
The Fortinet Security Fabric is composed of several key pillars. I will give a short insight into four of these pillars. The first is FortiGuard AI-Powered Security, these services are powered by FortiGuard Labs' machine learning and artificial intelligence models. Another pillar is Secure Networking, which addresses digital acceleration challenges by tightly integrating network infrastructure with advanced security across all edges. Also, Zero Trust Access is one of the key pillars. This is no surprise because in 2023 zero trust will also be a hot topic. Fortinet's Zero Trust Access securely connects applications hosted everywhere with users working from anywhere. Their Cloud Security solutions deliver visibility and control across cloud infrastructures, enabling secure applications and connectivity in the data centre and across cloud resources while maximizing the benefits of cloud computing.
CrowdStrike
CrowdStrike marries advanced endpoint protection with intelligence since it was founded in 2011. The CrowdStrike Falcon endpoint protection platform was built from the ground up to address the challenges posed by modern attacks and to stop breaches. It delivers a single lightweight agent for prevention, detection, threat hunting, response, remediation, vulnerability assessment and IT hygiene.
Their Falcon prevents framework touts five-second visibility on all endpoints, past and present, while also reducing cost and complexity. CrowdStrike provides cybersecurity services that include threat intelligence, next-gen antivirus, incident response, ransomware blocking and endpoint detection and response.
In the CrowdStrike 2022 Global Threat Report, they report on today's cyber threats and adversaries. The report covers real-world scenarios and observed trends in attackers’ ever-evolving tactics, techniques and procedures and offers practical recommendations to protect your organisation in the coming year. Last year CrowdStrike saw that the threat landscape became more crowded as new adversaries emerged. Notable adversary updates include:
- 21 newly named adversaries
- 45% increase in interactive intrusions
- 62% of attacks were malware-free
- 82% increase in ransomware-related data leaks
- 1 hour and 38 minutes average eCrime breakout time
- 170+ adversaries tracked
In Q2 of 2022 CrowdStrike was named a leader in the Forrester Wave™ for Endpoint Detection and Response providers. With Falcon Insight they stay true to their DNS as an endpoint-first security tool while methodically expanding into XDR and Zero Trust.
Acquisitions by CrowdStrike
In 2022 CrowdStrike acquired one security company:
- Reposify: a provider of an external attack surface management (EASM) platform that scans the internet for exposed assets of an organisation to detect and eliminate risk from vulnerable and unknown assets before attackers can exploit them.
Cisco
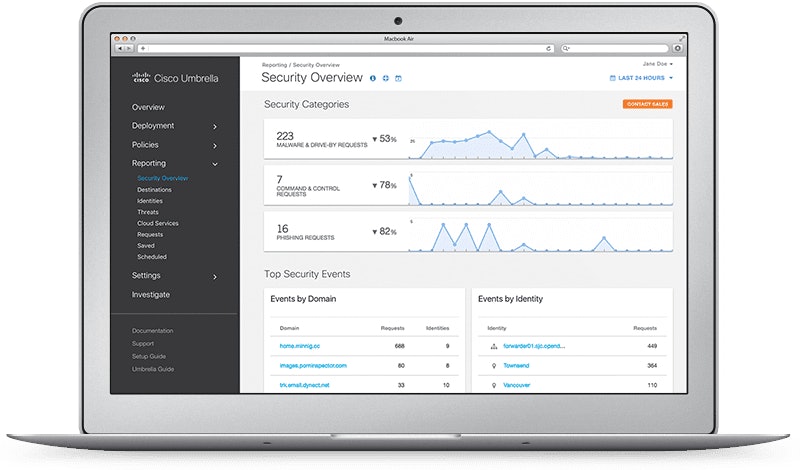
Cisco Umbrella is a cloud security solution providing secure access to the internet and secure usage of cloud apps. Having developed a cloud-delivered firewall, a web gateway, DNS Security and CASB solution, Cisco Umbrella proves to be an effective cloud-native platform solution, providing the multi-layered approach many security engineers look for. It’s a smart proxy only routing traffic to risky destinations through its network while safe content is accessed directly with no delay.
The investigative tool helps you to see relationships between domains, IPs and malware. Cisco’s Threat Intelligence not only investigates attackers’ infrastructures but is also able to predict future threats. In this way, current and developing threats such as malware can be exposed, so incident investigation and response times reduce significantly.
In April 2022 Cisco introduced the Secure Firewall 3100 Series. This series is designed to support more hybrid workings. Whether working from home, airport or coffee shop, remote workers can enjoy up to 17 times faster VPN performance. The firewalls use machine learning technologies to passively identify user applications and potential threats in encrypted traffic, without decryption, to detect more malware.
The Cisco firewall products are marked as a strong performer in the Forrester Wave™ for Enterprise Firewalls in Q4 2022. The main reason they are not a Leader is that customers are slow to migrate from legacy ASA firewalls to the Cisco Secure Firewall Threat Defense (FDT) NGFW product family.
Acquisitions by Cisco
In 2022 Cisco acquired Opsani, a cloud optimisation specialist. Not a security company, but still interesting as its managed technology and machine learning functionality allow companies to improve availability and capacity in an automated manner.
Netscout (Arbor Networks)
Securing your cloud against DDoS attacks is vital for service continuity. If you’re looking for critical aspects of DDoS protection, including the vital features to have in any DDoS protection product, Netscout is the cybersecurity company to turn to. Formerly Arbor Networks, Netscout is on its way to completing the second decade of its Anti-DDoS lifespan, offering the classical combination of Arbor Sightline and TMS that continues to prove its effectiveness across many industries.
Arbor Sightline is an anomaly detection system. It is based on sampled netflow, capable of performing enhanced reporting, alarming, automated mitigation in multiple phases and can even be triggered by their Availability Protection System (APS).
An extra powerful feature is that any third-party script or application for mitigations can be triggered by external and existing logic.
Important to note is that TMS’s detection service also makes use of (and helped set up) the ATLAS Intelligence Feed (AIF), providing insight and expert analysis for DDoS protection. With the Arbor Security Engineering & Response Team (ASERT), dedicated to discovering and analysing emerging threats and developing targeted defences, Arbor has both visibility and remediation capabilities at nearly every tier-one operator and a majority of service provider networks globally. ASERT shares this operationally viable intelligence with hundreds of international Computer Emergency Response Teams (CERTs) and with thousands of network operators via inband security content feeds. Being part of ATLAS, actively monitoring Internet threats around the clock and the globe via ATLAS, ASERT gives you another good reason to consider Arbor’s anti-DDoS solutions.
Netscout regularly publishes its DDoS threat intelligence report. In the first half of 2022, they presented the following key findings for the EMEA region:
- DDoS attacks altered the entire regional cyberspace as a result of the ongoing conflict between Russia and Ukraine.
- Geopolitical influence and infrastructure offloading resulted in attacks spilling into neighbouring countries.
- A global trend in more TCP-based attacks was clearly evident in EMA with TCP ACK floods eclipsing any other DDoS attack vector in the first half of 2022.
Juniper Networks
According to Forbes Juniper has wisely pivoted its products to software that can be delivered from the cloud. This is a smart move as the market for on-premises routing and proprietary enterprise hardware is stuck in a slow-growing rut. Of course, they still support their enterprise customers that want to use on-premises hardware. Juniper has expanded its addressable market with a comprehensive cloud-based security stack, as well as software solutions.
In February 2022 Juniper introduced Juniper Secure Edge, the newest addition to its SASE architecture. This solution delivers Firewall-as-a-Service (FWaaS) as a single-stack software architecture, managed by Security Director Cloud, to empower organisations to secure workforces from any place. A couple of months later Juniper expanded its SASE offering with the addition of CASB and advanced DLP capabilities to its Juniper Secure Edge solution. With this addition, Juniper can connect organisations existing security posture to data and apps that live outside the network's physical perimeter. When this is combined with Juniper's SD-WAN solution driven by Mist AI, they are the first to offer a full-stack SASE solution with visibility into both the edge and the data centre.
The Juniper SRX Series NGFW is marked as a Strong Performer in the Forrester Wave™ for Enterprise Firewalls in Q4 2022. Juniper’s appliance performance is superior, and customers describe the SRX TLS decryption capabilities as above average. The main reason they are not a Leader is that it integrates well with the network, but its supporting services fall short.
Acquisitions by Juniper Networks
In 2022 Juniper acquired one company:
- WiteSand: Cloud-based network operations management solution provider. Its products include instant-based NAC, network provisioning, network monitoring, and flow analytics.
F5
F5 has a broad suite of enterprise security solutions. Their solutions are available in any environment, wherever you deploy your apps: on-premises, private-, public- or multi-cloud. These performance and security services include load balancing, DNS services, web application firewalls (WAF), identity and access federation, and DDoS mitigation.
According to F5 applications power businesses of all sizes. Critical as they are, applications can put your business at risk as applications and their data are a focal point for today's attacks. To protect your business they have several security solutions. We'll explain a few.
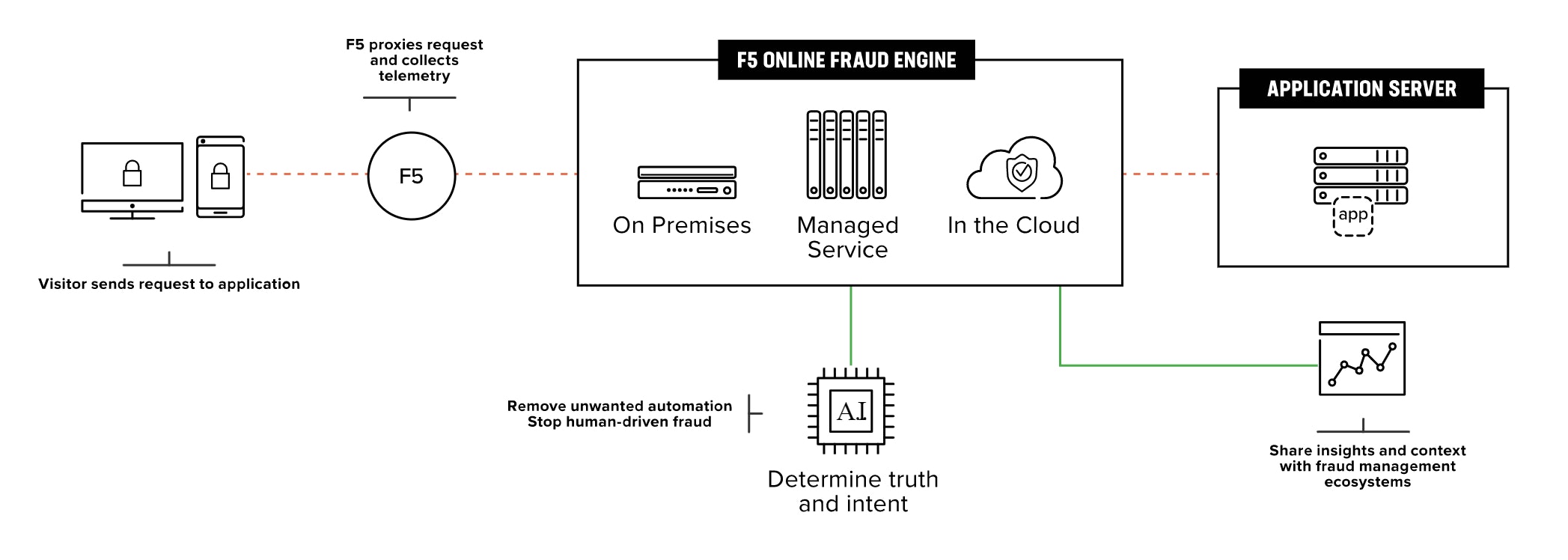
Traditional DDoS solutions focus on a narrow range of attacks. The DDoS Hybrid Defender of F5 provides a greater depth of defence. It's a multi-layered defence that protects against blended network attacks and sophisticated application attacks. While enabling full SSL decryption, anti-bot capabilities, and advanced detection methods—all in one appliance. With F5's Advanced WAF you are protected against the latest attacks with behavioural analysis, proactive bot defence and application-layer encryption of sensitive data such as login credentials.
According to F5, annual fraud losses are set to exceed $48 billion by 2023. The rapid growth of digital channels for consumers to transact and the endless availability of personally identifiable information, including stolen credentials increase the risk of businesses—and their customers—of falling victim to online crime. F5 protects financial services and online merchants with an integrated platform solution that brings security and fraud teams—and data—together to stop fraudsters in their tracks. F5’s large data set applied to its AI/ML algorithms makes it possible to enable more predictive and precise prevention measures than any other solution—with fewer false positives. They do this with their solutions Prevent Account Takeover; which stops account takeovers (ATO) before it leads to fraud, lost revenue and damage to customer loyalty, Stop Human-Driven Fraud; which prevents fraud in real-time without impacting the user experience, and Mitigate Bots and Abuse; it removes unwanted automation leading to a variety of attacks that cause fraud.
Trellix
In January 2022 the launch of Trellix was announced. A new business providing extended detection and response (XDR) to organisations with a focus on accelerating technology innovation through machine learning and automation. Trellix was born after STG acquired both FireEye and McAfee Enterprise in 2021.
Trellix brings you a living XDR architecture that adapts at the speed of threat actors and delivers advanced cyber threat intelligence. The XDR platform connects all Trellix technologies and a broad network of over 650 vendor partners and tools to provide a seamless SecOps experience in one place. According to a survey of IT security and SOC decision makers, respondents said they spend 27% of their time dealing with false positives, while actual threats can easily be missed. With increased intelligence, XDR helps you not only quickly detect threats but predict attacks—and even automate responses in real-time. Powered by AI and machine learning, XDR doesn’t remove the human element, but rather enhances the existing human knowledge and experience.
Next to XDR, Trellix also offers several other solutions such as endpoint security, data protection and EDR. They deliver device-to-cloud security across multi-cloud and on-premises environments. Their solutions protect data, defend against threats, and provide actionable insights through an open platform and the largest threat telemetry network.
Nomios’ cybersecurity vendors
These vendors form the core of our cybersecurity architecture that aims at supporting our customers in the transition to a Zero Trust Access and SASE architecture. Combining the innovation power of these cybersecurity leaders and the Nomios local skilled resources are key success factors for a successful security architecture transition for maximum security, lower costs and the best user experience with IT services to increase productivity.
However, as each organisation is different, you need the solutions that fit your situation best. We at Nomios are happy to help you in your search for a cybersecurity solution.
Do you want to know more about this topic?
Our experts and sales teams are at your service. Leave your contact information and we will get back to you shortly.