Nearly all IT professionals (~95%) agree that passwords pose real security risks to their organisation. People have been using weak passwords for as long as we can remember, then there's mishandling passwords (writing them on post-its) and reusing the ones we feel comfortable with. Not exactly best practices according to LastPass, but also no shocking news, as we're all guilty as charged.
Do you recognise yourself in this video?
Just watch it, at the very least you'll have a good laugh.
Passwords are too weak
Among the top frustrations for employees is changing passwords, remembering the previous 100 passwords and not being able to re-use them. This makes password management a tedious part of the job and surely doesn't really add any security if done improperly. It also increases the additional labour required for simple hygiene; just think about the time wasted on password resets.
In order to combat weak passwords, we need to be building security habits that aren't overly complex and actually make life easier, instead of harder. Weak and/or re-used passwords pose a real threat to organisations because they're typically the one thing between your data and bad actors. The bad actors have done a marvellous job in indexing the most common passwords to make password spraying attacks easier and more effective. You just have to look for the right dataset, taking culture and language into account. Not just bad actors, but the good guys also index weak passwords, they do it for awareness reasons.
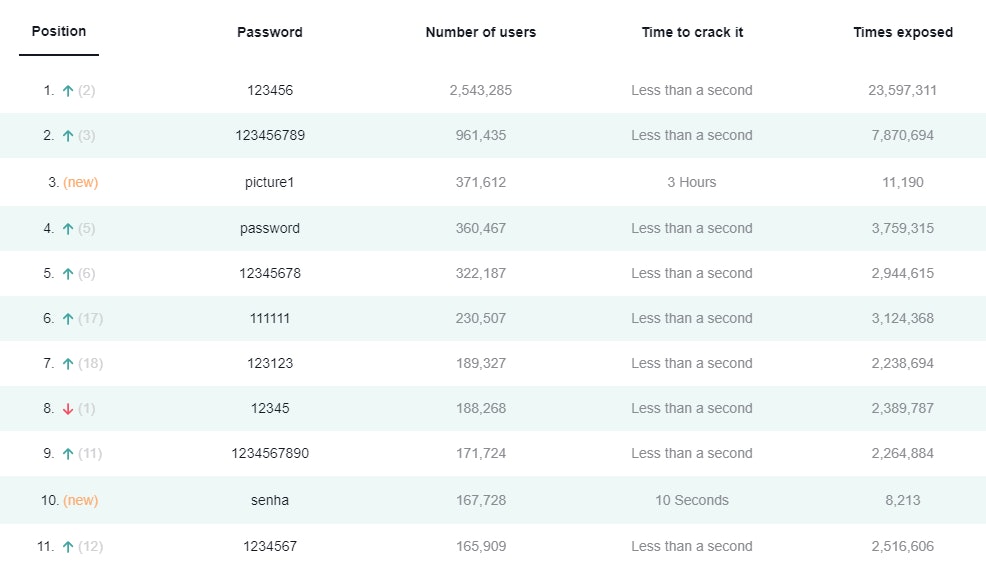
See below the top 11 of most used passwords for 2020 in the world. View all 200 most common passwords.
Leaked passwords
Let's assume, for the sake of argument, that you have adopted on-par security habits, even if you do everything right, your secure passwords might be leaked. Your responsibility is only a part of the puzzle. The other side (the application), should also take measures to safely store the information you use to authenticate. This means they should hash the secret info and secure the systems and infrastructure on which this information is stored and accessible.
Information leaks all the time, in the past months we've seen TicketCounter.nl (August 2020), Eneco (January 2021), GGD GHOR (January 2021), AlleKabels.nl (Februari 2021), NAM (March 2021), RDC.nl (March 2021), DS-IT (April 2021), Gemeente Amsterdam (April 2021), Heijmans (April 2021) and a few weeks back New York Pizza (June 2021). It doesn't take long for this information to surface on the web, in fact, you can quite easily find combined (COMB) datasets with a quick google. COMB stands for combination and is basically a combination of leaks, sorted for ease of use.
Findings of my research on the first 100 million combo's from Cit0day are corroborated by research done by NordPass.
Dehashed
The bad guys are typically a few steps ahead of us, there's no silver bullet, nor a 100% safe system. At some point, we should assume systems are going to be breached and data leaked. If you've taken the measures prescribed by the various best practices, you are at least safer. Unfortunately, there are a lot of tools readily available to 'crack' even the hashed passwords.
Let's use this example:
Someone "found" a dump of leaked credentials, note that this information is quite easy to find.
"It’s well known that most people base their password on a word, in various forms:
- Just a word (potentially with different capitalisations) — Password
- A word followed by some numbers/symbols — monkey! or Coffee12
- A word with ‘leet speak’ applied — p4ssw0rd or f4c3b00k
- Multiple words stuck together — isthissecure"
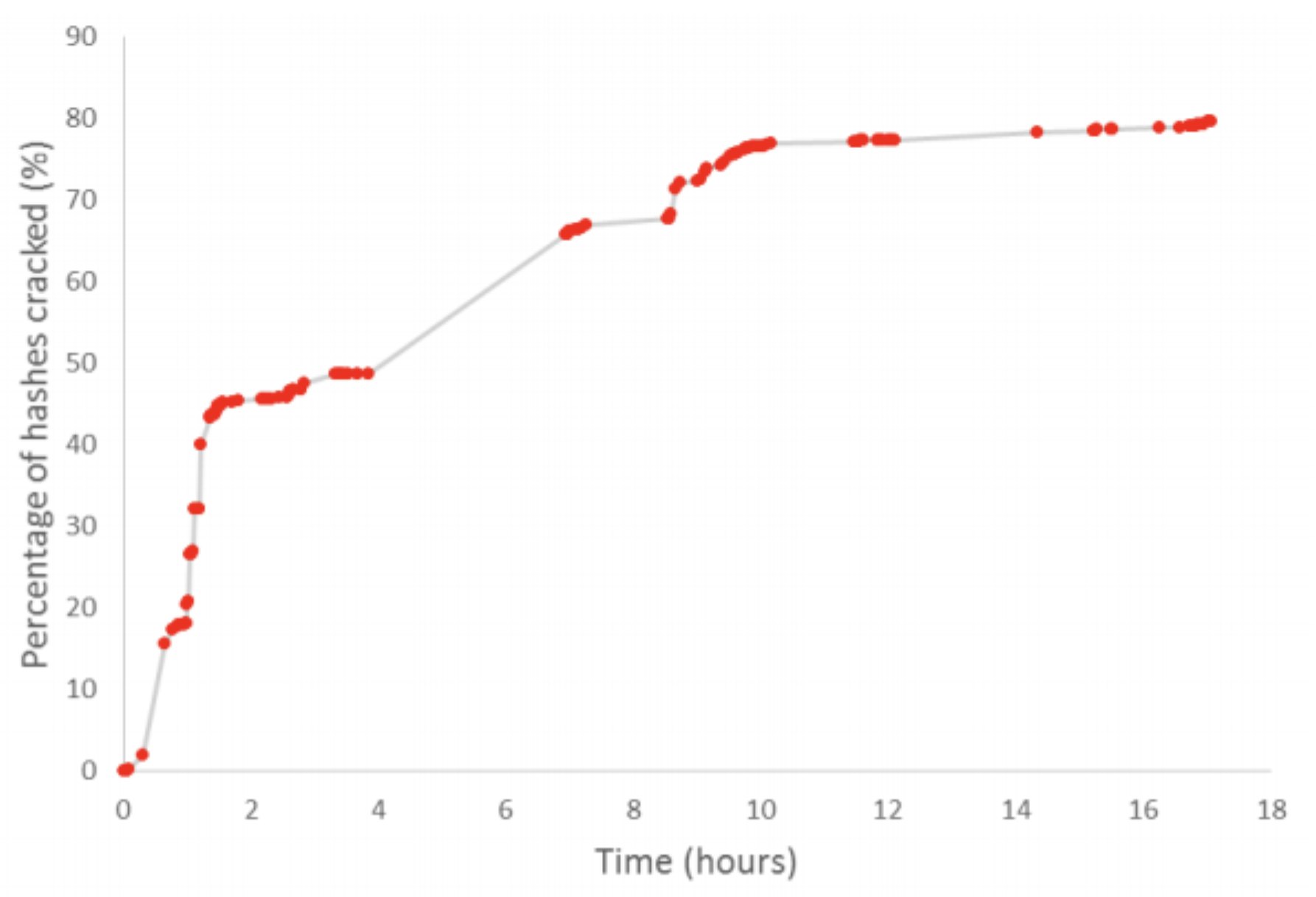
In order to crack hashes you typically use highly efficient tooling, which is available for free (open-source), like Hashcat. I will not dive deeper than this, you can read the whole article online. Apart from tooling, you need a strong processor. You don't even need to own the hardware anymore, you can 'rent' an Nvidia Tesla K80 GPU on AWS for as little as $0,90/hour. It's able to calculate ~800 million SHA-256 hashes per second… let that sink in.
In the article the author used a dataset of 14 million credentials and reached the following milestones:
- 2 hours: 48% of the passwords were cracked
- 8 hours: nearly 70% of the passwords were cracked
- 20 hours: over 80% of the passwords were cracked
In summary: "20 hours. $0.90 per hour. That’s just $18 spent to have 80% of 14 million passwords cracked."
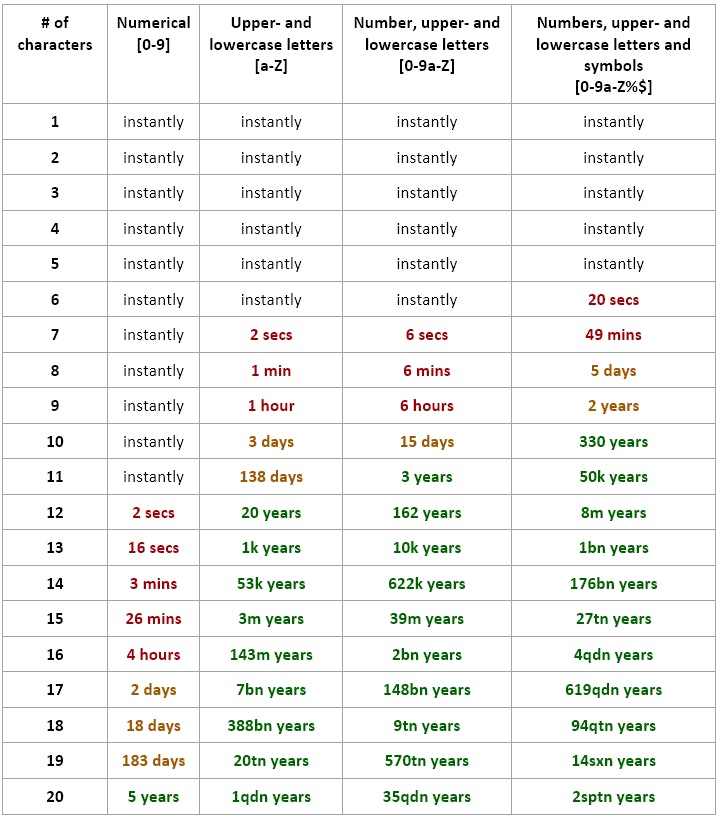
The below table depicts how long it would take for an NTLM hash (i.e. Windows passwords) to be cracked. Note that these numbers may vary across research papers, these are pretty up-to-date and pertain specifically to NTLM hashes and the use of AWS compute available in 2020.
Note: the above table is based on 632GH/s cracking power (AWS p3.16xlarge @ $25/hour) for NTLM hashes, The Security Factory.
Multi-factor authentication (MFA)
This is why we need MFA sooner, rather than later. This will add a 'factor' to the login sequence, in other words, you need more than just your username + password (something you know). Because the other factors are not found online, it's way harder for the perpetrator to get into your accounts. Let me emphasise, it's not a silver bullet, there can be bugs in the system using or providing MFA functionality. But at least you've done all you can do in this regard.
What is MFA?
- Something you know -> e.g. a password
- Something you have -> e.g. your phone or a token
- Something you are -> biometrics; e.g. face ID and fingerprints
- Somewhere the user is -> geolocation
Passwordless, is that a thing?
Microsoft has already adopted this new idea, why should a password be safer than something that you have and are (still two out of the three tenets for MFA)? You just have to fill in your account login (e.g. your email address) and the system will send a push notification to your phone. This push notification can only be viewed if you authenticate on your phone with biometrics (e.g. fingerprint or face ID). This makes it way more difficult for bad actors to abuse your account because it's more difficult to get in, they will need your phone and you.
We will see more adoption of this idea because it eliminates one of the fundamental IT problems: password management. No more password reset requests or remembering all these different passwords or issues with password managers that don't integrate properly. Just a new way of signing in, and preferably one that holds your authentication for every app that you need for work until something changes in your session/behaviour. For example, your IP address, turning off security features on your laptop, privilege escalation etc.
In conclusion: what should I do?
So, what you're saying is that I should consider passwords pretty much compromised by default? Well yes and no, you can't go through life without passwords (yet), so at least use different passwords for different sites/services; if a passwords leaks, the damage is contained to that one account.
Advice #1 use a password manager
A little bit of personal advice, passwords are annoying (I know), but they’re pretty much the only thing between you and people trying to abuse some(if not most) of your accounts. Corporates tend to ask you to change your passwords frequently, which is a solid countermeasure, but not very user friendly. It’s therefore advisable to use a password manager and have it generate ridiculous passwords for your online accounts (16+ characters). You can determine for yourselves if you feel safe to store all your passwords there, in general, it's safer than the alternative (weak and reused passwords).
Which password manager is the best? There no easy answer, it boils down to two things: safety (most password managers score well in this area) and ease of use (this is quite personal). So try one or two before you buy (if you're going to buy).
Advice #2 use MFA whenever (and wherever) possible
On top of that, certainly for sensitive accounts, please enable MFA. Don’t worry if you haven’t heard of it, or if you call it something else. This typically requires you to use your username + password and a code/push notification in an app on your mobile phone (or tablet).
Drawing money from an ATM is comparable, you need the bank card and the pin code; something you have and something you know. You can use any of readily available authenticator apps; Microsoft Authenticator, Google Authenticator, DUO Mobile, etc. Even today, in 2021, many accounts are protected by weak passwords (and lots of passwords are leaked every day) and adding MFA makes it a whole lot more difficult for hackers to get into your accounts.
Tip: try enabling MFA on LinkedIn/Facebook/Instagram/Personal email, etc. This is easy to set up and gives you extra security.
Enable it, open your Authenticator App, scan the QR-code (press the plus sign, typically on the right side of the screen) and you’re all set! You have just upped the ante on your security game.
PS: while you're at it, you might want to change your password if you've never done this (especially if you joined before 2013).
Advice #3 stay vigilant!
Keep people from glancing at your keyboard when typing in passwords/passcodes etc. Setup monitoring of your account and/or regularly check the activity logs. You can also setup Google Alerts, to notify you when something about you pops up on the internet (note: it will not detect everything of course). It's quite easy, browse to google.com/alerts (and if necessary, sign in); here you can configure what to monitor.
Another tip is to register at haveibeenpwned.com; this site indexes leaks and notifies you if you're email has been in any of the known leaks.
If you have any questions, want a sparring partner, or you're curious about what this all means? Feel free to contact us.

Cybersecurity
Top cybersecurity companies to watch in 2025
We selected the top cybersecurity companies to watch in 2025, who have successfully differentiated themselves from other players in the market.

Mohamed El Haddouchi

Cybersecurity
The latest cybersecurity challenges
Explore the latest cybersecurity challenges, from AI-driven threats to quantum risks, impacting organisations in an evolving threat landscape.

Usman Khan

Network segmentation Network security
Prevent lateral compromise with micro-segmentation
Why network micro-segmentation matters for network security and how it helps mitigate the spread of lateral compromise.

Herwig Mertens
Do you want to know more about this topic?
Our experts and sales teams are at your service. Leave your contact information and we will get back to you shortly.