Zero Touch Provisioning or ZTP is a term that appears increasingly on the feature list of networking products. ZTP can be found in switches, wireless access points, (SD-WAN) routers, NFV platforms and firewalls.
What is it and how do we benefit from it? Do all ZTP implementations offer the same functionality and are they equally easy to use? In this blog, I will dive deeper into what vendors offer, what differences there are for ZTP implementations and how ZTP impacts us.
What is Zero Touch Provisioning (ZTP) and what does it do?
As the name Zero Touch Provisioning would suggest, the goal is to install a networking appliance somewhere without someone needing to configure it locally. A new or replacement device can be sent to a site, physically installed and powered up by a locally present employee without IT skills. This is where the ZTP feature comes in, to carry out the configuration and connection to the management system. I will describe how this is done later on in this blog post.
How does ZTP help?
Manual configuration is laborious, prone to errors, costly and time-consuming. Someone with basic configuration skills and a laptop has to go onsite and configure the device for basic operation before we can complete the configuration from the central management system. Alternatively, we can first send the device to a central location where it is staged before it is sent to the final location for installation. This is also costly as it requires shipping the device twice, which might include passing through customs twice. This runs the risk of accidentally shipping an appliance with the IP address destined for site A to site B.
With ZTP a device can be shipped directly from any warehouse to the final location and installed as soon as it arrives, being up and running within minutes of installation. This dramatically reduces the lead time, the number of hours spent on an installation and the number of configuration errors. These are potentially huge benefits when you have many sites with no IT staff or new sites that are being opened frequently, such as (pop-up) stores or temporary offices. ZTP is also useful for any home-office type setup.
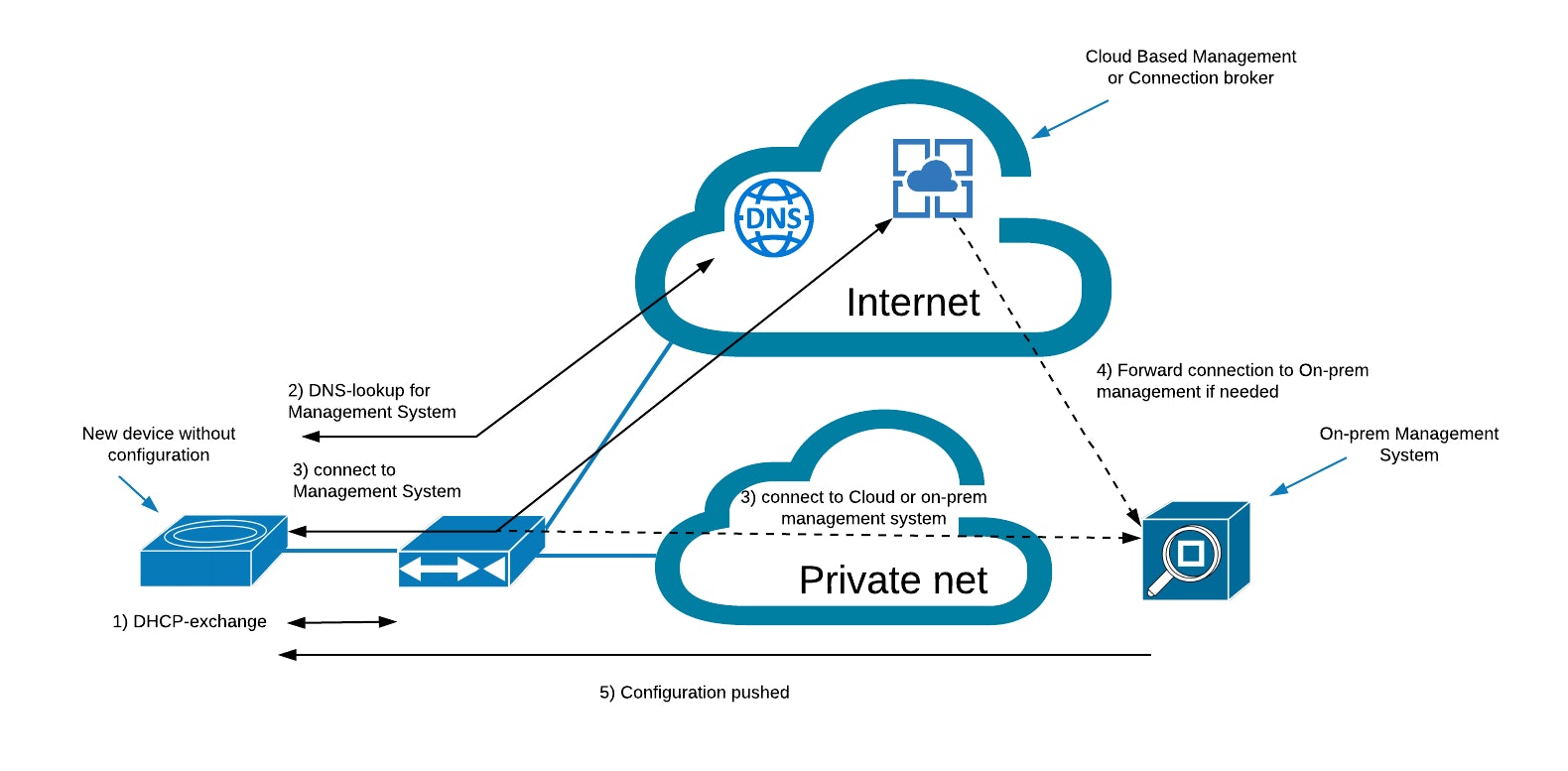
How does ZTP work and what is minimal or one-touch provisioning?
This is where it gets interesting. ‘Zero Touch’ suggest that whoever does the physical installation doesn’t need to do anything about configuring the device, so the device itself (using its factory default configuration) needs to be able to find the management system that will give it its configuration for that location and the organisation. Not all ZTP implementations are truly ‘Zero Touch’ though, so sometimes you will also come across terms like ‘minimal touch provisioning’ or ‘one-touch provisioning’.
The first thing a device needs to communicate is an IP address. Luckily Dynamic Host Configuration Protocol (DHCP) is pretty ubiquitous nowadays so that helps ZTP in the first stages. DHCP will also provide the address of the gateway, the local domain name and the location of a DNS server. If DNS is not provided or unreachable, the device can always try to use Google’s DNS service at 8.8.8.8. DHCP also has some optional fields that can be used to provide the device with an IP address of the management system. The factory default configuration may also have a pre-defined name for the management system (i.e. “orchestrator”) in its default configuration that it will combine with the domain name DHCP gave it to do a DNS lookup. This then becomes a query for a host like “orchestrator.example.com”. This needs to be resolvable in the DNS to the IP address of your management system, so it does require preparing your network once. The same is true for serving the management address via DHCP options.
Once the device has an IP address and knows where to go for its configuration, there may be other obstacles that need to be overcome. Often the WAN connection is an Internet link that may require activation through a portal or by authenticating the PPoE or PPoA connection. In such cases, manual intervention is needed and the ’Z’ in ZTP becomes an ‘M’. Another obstacle could be a firewall preventing the connection from being established. In that case, the firewall rules need to be adjusted, but this can usually be done remotely. Outbound HTTPS is usually permitted, so that is the de-facto protocol to connect to the management system.
Alternate solutions don’t use DNS or a DHCP option to learn the location of their configuration server. One vendor touts ZTP as a feature but requires a user to log in via the console port and enter a CLI command to set the configuration server IP address.
More and more vendors are offering a cloud service to support the configuration and ZTP-process, Cisco Meraki, Riverbed, Citrix and Juniper Networks are among those. All that is required is registering the serial numbers of the devices purchased and the vendor will ensure the devices are correctly registered and visible under your management portal account. The device can then be fully configured and managed via the cloud.
For those of you that don’t want their management of the network in the cloud but on-prem, there are options. The vendor’s cloud service will still be the go-to point for devices with a factory default configuration, but it will be forwarded to the on-prem configuration server. Obviously, any cloud-based provisioning scheme requires access to the internet, either directly or via the company network.
‘Minimal touch provisioning’ with phone apps
Remember how you used to configure your home devices such as Ethernet-over-Power extenders and Access Points? Often the box would include a CD with a little program that would find the new device on your LAN and help you configure it. Those days aren’t gone yet but have moved on a bit. Some vendors now offer minimal touch provisioning through a phone app for example. Assuming there is someone on site who is able (and willing) to install such an app on their phone and is able to connect to the device on the local LAN or via a default SSID on the device (obviously it needs to have Wi-Fi capabilities for that). Upon installation, the app connects to the configuration server and the new device and acts as a proxy between them, either over the local network or through a mobile data connection. Often the camera is used to scan the device’s barcode sticker to determine the Serial Number and model.
Any security issues with ZTP?
Authenticating the device and ensuring its connection to the correct management domain is important. It would be a bit embarrassing if a wrong serial number is registered and your device is now configured by another (malicious) entity. A lost (or stolen) device also shouldn’t automatically be accepted into your infrastructure. Imagine your SD-WAN router in the hands of an attacker who connects it to the Internet and automatically gets direct access to your internal network. Not something you would want. Any cloud-based service also needs to be secure to prevent attackers from inserting their devices into your domain or taking control over them.
ZTP in summary
ZTP is becoming more widely supported as vendors realize their equipment could now be installed anywhere and installation is a major cost factor. Have a good look at ZTP if you frequently install devices in remote locations without local IT staff. Test to see if the ZTP features for your equipment work in your environment and if adjustments need to be made for it to work. ZTP implementations differ greatly between vendors and not all are truly ZTP. There may be some basic requirements that need to be met for ZTP to work, such as DHCP and others that depend on DNS and access to the Internet. Also, make sure a ZTP function can’t be used as an attack opportunity on your network.
Do you want to know more about this topic?
Our experts and sales teams are at your service. Leave your contact information and we will get back to you shortly.